Deserialization of Untrusted Data
Serialization is the process of turning an object in memory into a byte stream that can be stored and restored later. Deserialization is the reverse of that process, taking the byte stream and rebuilding it into an object in memory.
Overview
Deserialization mechanisms are abused and repurposed for malicious effect when operating on untrusted serialized data. For example, code can be injected into the objects to be serialized, and then later executed upon deserialization, much like persistent XSS attacks. Attacks against deserializers have been found to allow denial-of-service, access control, privilege escalation and remote code execution (RCE) attacks.
Waratek uses a virtualization-based approach to runtime application self-protection or RASP. This allows the Waratek to create a smart, restricted dynamic micro-compartment that prevents malicious operations from executing. Waratek's deserialization protection capability is activated when deserialization occurs and is automatically disabled once it has completed.
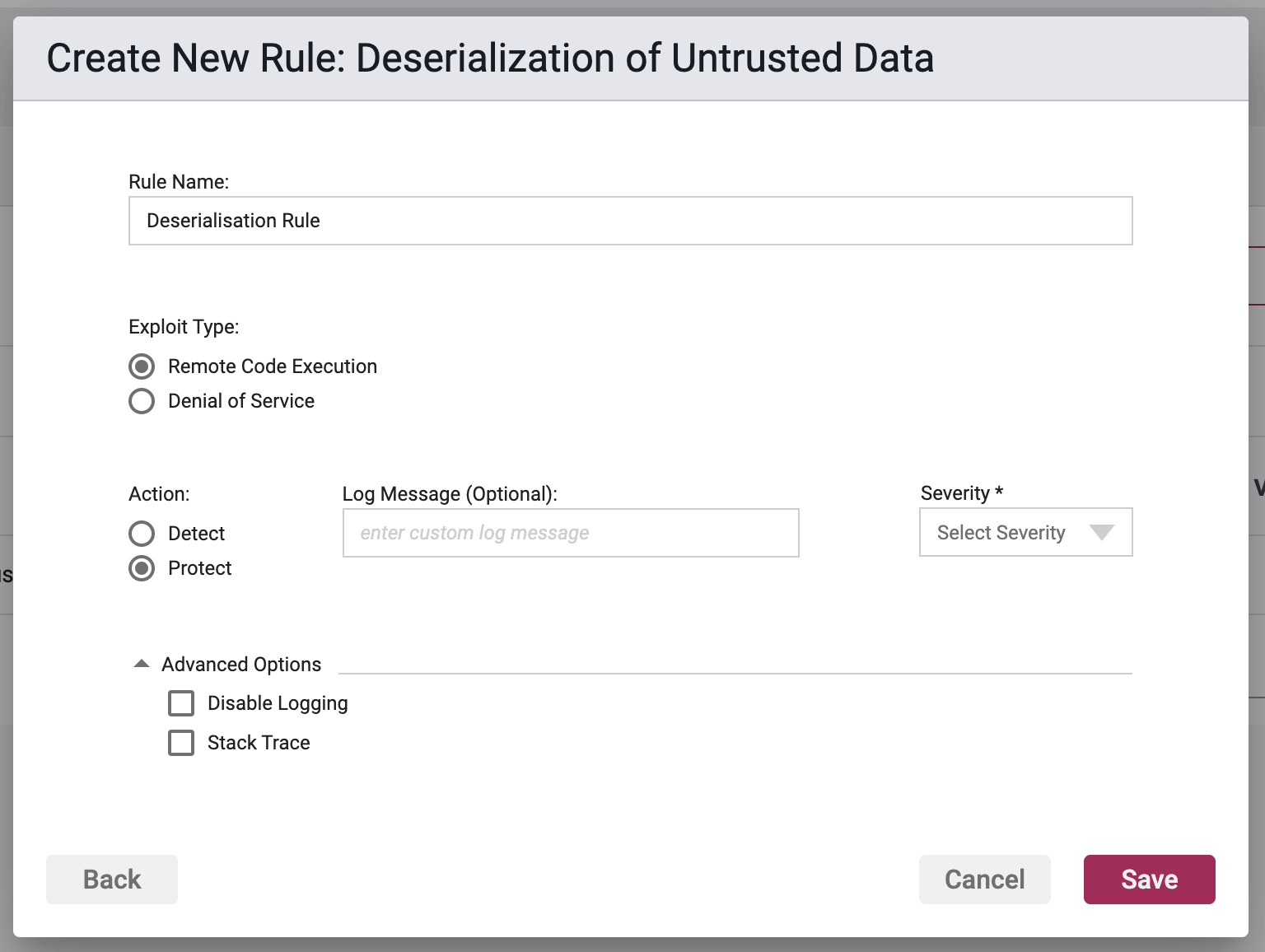
Rule Options
Exploit Type
- Remote Code Execution - This option protects against deserialization payloads that perform privilege escalation and Remote Code Execution (RCE).
- Denial of Service - This option protects against deserialization payloads that perform Denial of Service attacks (DoS) on the host. For example, a malicious deserilization payload can cause the process to loop indefinitely and consume all available CPU resources on the host (e.g. billion laughs attack).
For each Remote Code Execution or Denial of Service configuration, the Agent only allows one rule to be specified.
Action
- Detect - The Agent will detect the attack, it will log the event to the event database, and the event will be viewable on the Security Events pages in the Portal, but the Agent will take no further action.
- Protect - In addition to the Detect actions, the Waratek Agent will also actively prevent the attack from succeeding.
Log Messaging
The logs provide a message field, which can be customized. Text entered here is the message that will be seen on the log files when the rule has been triggered, regardless of the Action. If the field is left blank, then the default logging message will be displayed in the message portion of the event log.
Severity
The log files allow you to select a custom severity level for the event: Low, Medium, High or Critical. A severity is required, and there is no default selection.
Advanced Options
Disable Logging - By checking this option, no logging will be performed when a rule is triggered. Subsequently the Portal will not see these events, and they will not appear anywhere in the Portal, nor will they be searchable in Event Storage.
This option will be greyed out if the rule action is set to Detect.
Enable Stack Trace - By checking this option, when a rule is triggered, the stack trace will be included in the event log, and will be available for viewing in the Portal UI for each triggering security event.
Resources
More information on deserialization can be found at:
- https://waratek.com/blog/the-java-deserialization-problem/
- the CWE's community-developed website
- the OWASP Foundation's website
- Christian Schneider's blog