Open Redirection
Open Redirect is an input validation flaw that exists when an application accepts untrusted input that contains a URL value and does not sanitize it.
Overview
This kind of vulnerability could be used to accomplish a phishing attack or redirect a victim to an infection page. Since the redirection is originated by the real application, the phishing attempts may have a more trustworthy appearance.
An example of such an attack could be a weblink such as:
http://www.target.site?#redirect=www.fake-target.site
The victim that visits this URL will be automatically redirected to fake-target.site, where an attacker could place a fake page that resembles the intended site, in order to steal the victim's credentials.
The Hosts field and Allow action are only available on ARMR versions 2.7 and above
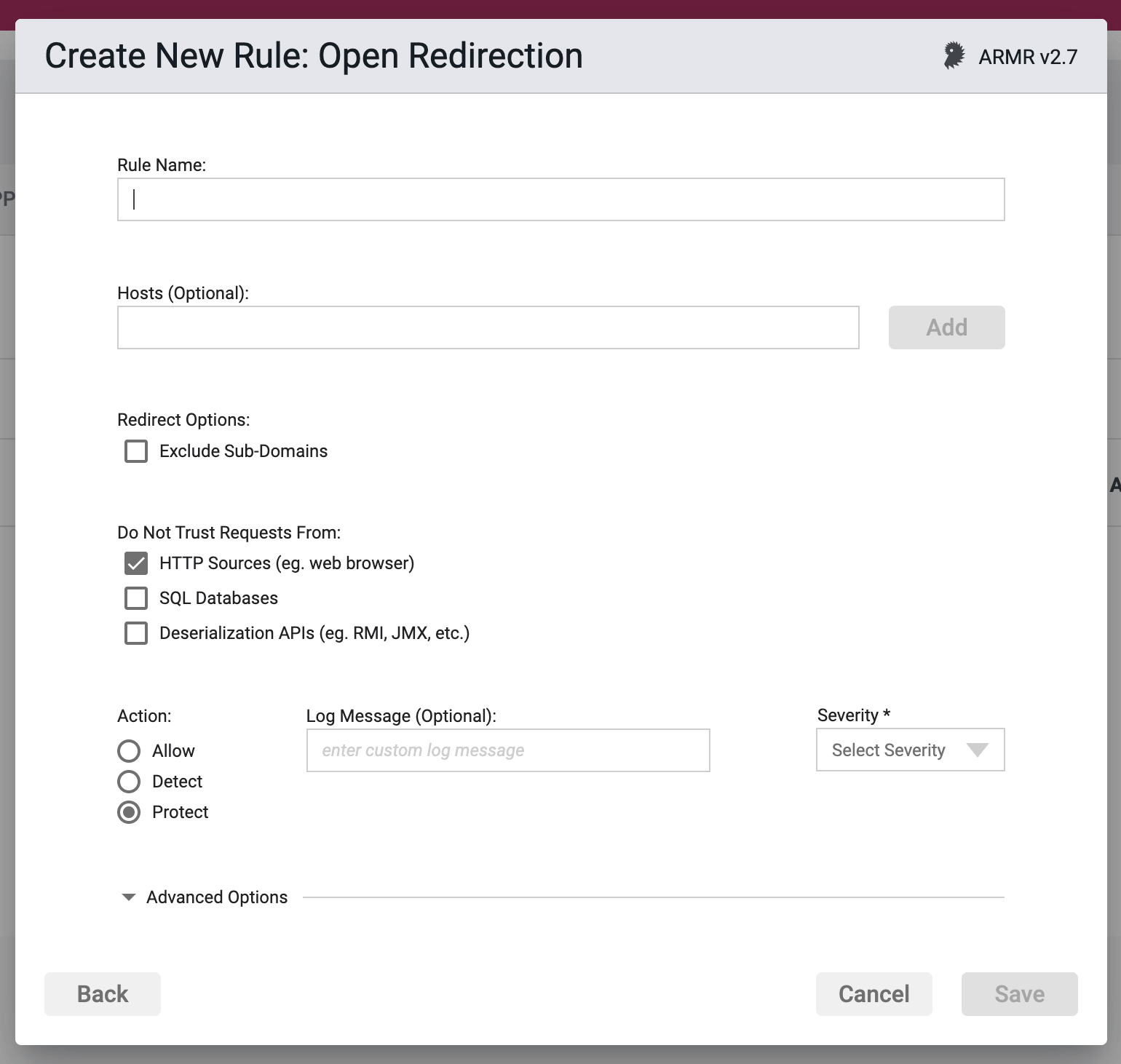
Rule Options
Hosts
A list of valid hostnames, fully qualified domain names or valid IP address can be added to this rule and whitelisted by selecting the allow action at the bottom of the form.
Exclude Sub-domain
When you select this option, only the top level domain will be protected against and sub-domains will not be processed as part of this rule.
Do Not Trust Requests From
These are the sources that Waratek will treat as untrusted.
- HTTP - Data received by the application from HTTP requests (e.g. from a web browser).
- Database - Data received by the application from a database.
- Deserialization - Data received by the application via deserialization APIs (e.g. RMI, JMX, java.io.ObjectInputStream, etc.)
You may select one or many of these but at least one selection is required. The default value is HTTP.
Action
- Detect - The Agent will detect the lookup of listed address(es), log the event, and the event will be viewable on the Security Events pages in the Portal, but the Agent will take no further action
- Protect - In addition to the Detect actions, the Waratek Agent will also stop the redirect.
The Agent allows only one Open Redirection rule to be specified in ARMR versions 2.6 and below
Log Messaging
The logs provide a message field, which can be customized. Text entered here is the message that will be seen on the log files when the rule has been triggered, regardless of the Action. If the field is left blank, then the default logging message will be displayed in the message portion of the event log.Severity: The log files allow you to select a custom severity level for the event ranging from Low to Critical. A severity is required, and there is
Severity
The log files allow you to select a custom severity level for the event: Low, Medium, High or Critical. A severity is required, and there is no default selection.
Advanced Options
Disable Logging - By checking this option, no logging will be performed when a rule is triggered. Subsequently the Portal will not see these events, and they will not appear anywhere in the Portal, nor will they be searchable in Event Storage.
This option will be greyed out if the rule action is set to Detect.
Enable Stack Trace - By checking this option, when a rule is triggered, the stack trace will be included in the event log, and will be available for viewing in the Portal UI for each triggering security event.