Cross-Site Request Forgery (CSRF)
CSRF is an attack that forces an end user to execute unwanted actions on a web application in which they're currently authenticated. The victim, authenticated to a website, is unknowingly tricked into performing an action on that website.
Overview
As an example, an attacker could send an email to [email protected] which contains a link. When the victim clicks on the link, the webpage that loads up can trick the victims browser into going to vmail.com's change password form and changing the password, all invisibly to the victim. As the attacker cannot see the results of the exploit, the exploit rarely results directly in data theft and more commonly results in the unwitting execution of an action. This could also do things like trick a victim into transferring money if the attack involves a bank website and if they are logged into the site as administrator, then the entire site can be compromised.
Rule Options
CSRF Protection
Same-Origin Headers - When an HTTP request is received by your application, Waratek Agent will perform Same Origin validation by matching the request's source origin headers against the allowed hosts and the request's target origin headers. If there is no match then Waratek will consider the request as malicious and will strip out all HTTP parameter and HTTP cookie information from the request before allowing the request to be processed by the application.
Synchronized-Tokens - When an HTTP request is received by your application, Waratek Agent will perform Synchronized Token validation by matching the victim's POSTed token to the token on the server.
Same-Origin Options
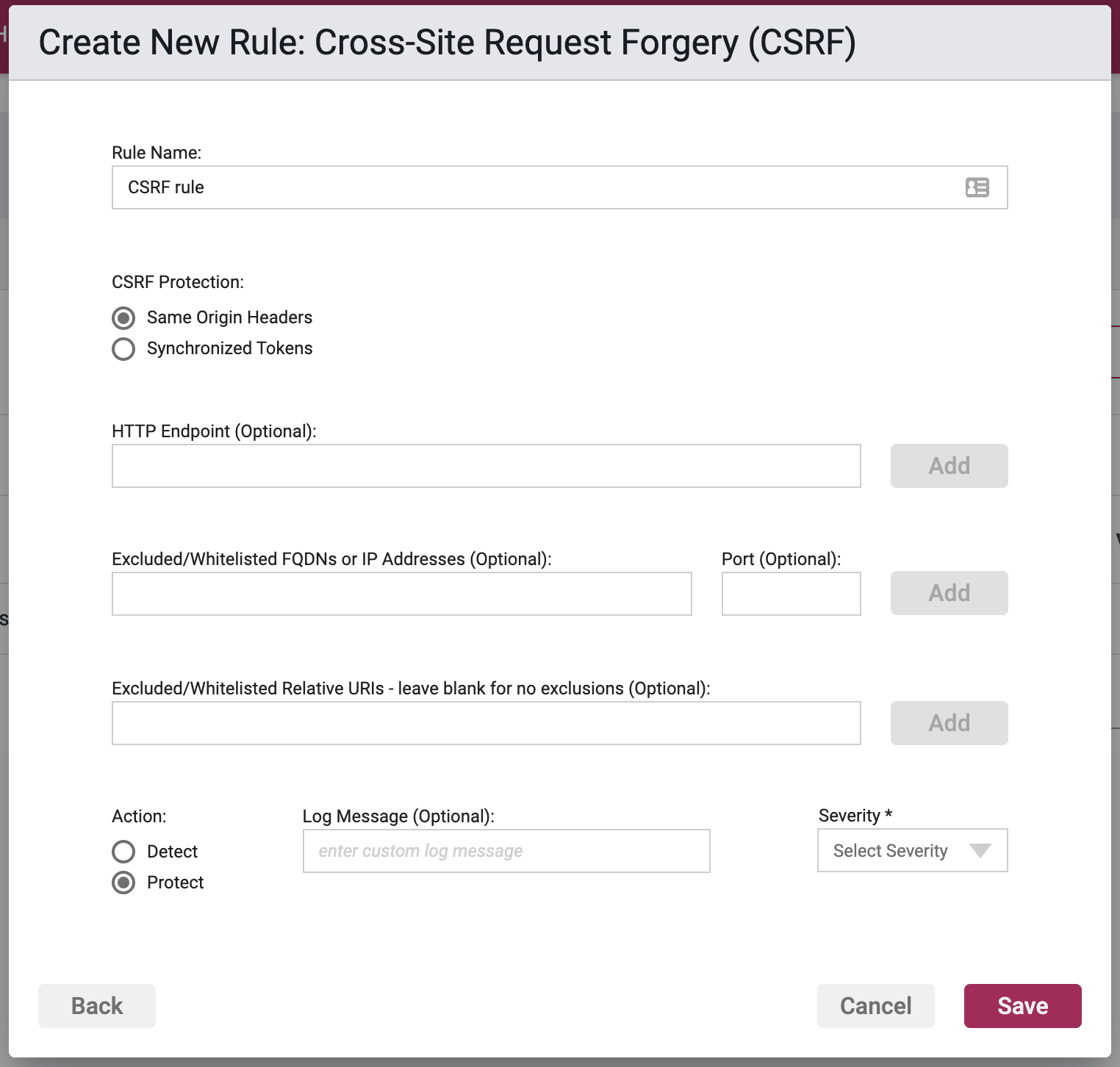
HTTP Endpoint (Optional)
Here the user may enter in a list of relative URIs to be protected, monitored, or whitelisted. A relative URI only includes the path portion of the URL, and not the domain. For example if the website address was http://www.victim.com/home/test.html, then /home/test.html is the relative URI or HTTP Endpoint.
The path within the relative URI must be absolute and begin with a leading /. In the above example /home/test.html is valid, and home/text.html is not. In addition relative paths may not contain .. or other similar characters denoting path shortcuts. For example, /home/test/user/test.html is valid, but ../test/user/test.html is not.
Excluded/Whitelist FQDNs
A list of FQDNs or IP addresses and optionally ports to be excluded from this rule's protection. An empty list means none will be whitelisted. Only single port values are accepted, not ranges. This defaults to an empty list.
A single CSRF Rule may apply to many different addresses. When you enter an IP address and port and click on the Add button, a table will appear under the fields (provided it is not already showing) and the entry will be displayed in the field. Entries in the table may be deleted or edited in place, using the table's actions.
- IP addresses must be v4. Fully Qualified Domain Names (FQDN) may be used here as well.
- An IP Address value of “0.0.0.0” indicates a wildcard value of Any IP address.
- A Port value of “0” or blank indicates a wildcard value of any port
Synchronized Tokens Options
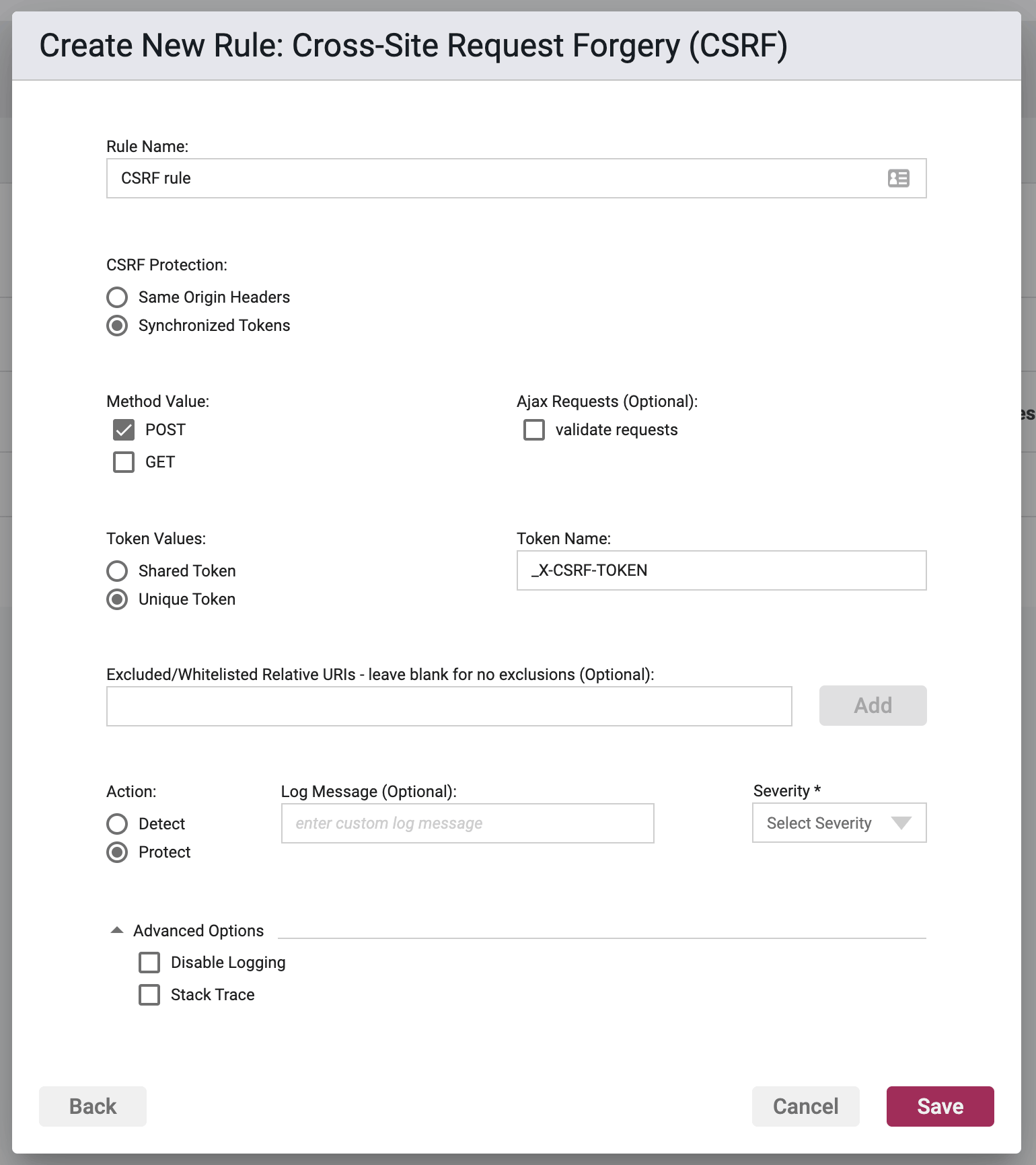
Method Value
The options are POST and GET. POST is selected by default. At least one option must be selected, and both options may also be selected. No selection will result in an error.
Ajax Requests
The only available option is to Validate (default, checked) or not Validate (unchecked) the requests.
- Token Value - The options here are Shared and Unique (default).
- Token Name - The default token name is _X-CSRF-TOKEN and filled in by default. You may fill in your own value. A blank field will result in an error.
Excluded/Whitelist FQDNs
A list of FQDNs or IP addresses and optionally ports to be excluded from this rule's protection. An empty list means none will be whitelisted. Only single port values are accepted, not ranges. This defaults to an empty list.
A single CSRF Rule may apply to many different addresses. When you enter an IP address and port and click on the Add button, a table will appear under the fields (provided it is not already showing), and the entry will be displayed in the field. Entries in the table may be deleted or edited in place, using the table's actions.
Action
- Detect - The Agent will detect the lookup of listed address(es), log the event, and the event will be viewable on the Security Events pages in the Portal, but the Agent will take no further action
- Protect - In addition to the Detect actions, request will be stopped.
For each of CSRF Synchronized Tokens and CSRF Same Origin Headers, the Agent only allows one rule to be specified.
Log Messaging
The logs provide a message field, which can be customized. Text entered here is the message that will be seen on the log file's when the rule has been triggered, regardless of the Action. If the field is left blank, then the default logging message will be displayed in the message portion of the event log.
Severity
The log files allow you to select a custom severity level for the event: Low, Medium, High or Critical. A severity is required, and there is no default selection.
Advanced Options
Disable Logging - By checking this option, no logging will be performed when a rule is triggered. Subsequently the Portal will not see these events, and they will not appear anywhere in the Portal, nor will they be searchable in Event Storage.
This option will be greyed out if the rule action is set to Detect.
Enable Stack Trace - By checking this option, when a rule is triggered, the stack trace will be included in the event log, and will be available for viewing in the Portal UI for each triggering security event.