XML External Entity (XXE)
The purpose of this rule is to prevent an attack on an application that reads and processes XML. These attacks are made possible through the use of the Document Type Definition (DTD). The XXE security rule addresses attacks, regardless of Java version or XML parser, by enforcing a strict policy of what the XML can contain.
This rule is only supported on ARMR 2.6 or higher
Overview
An XML External Entity (XXE) attack can occur in an application that reads in and processes XML. This can occur when reading in local XML files but is more common when the XML comes from a remote source as is often the case with web applications. If an attacker knows that XML can be sent to an endpoint where it will be processed, the attacker can send an XML that could make the application perform server side request forgery, read files from the local file-system, or even cause denial-of-service attacks.
XXE attacks are made possible through the use of the Document Type Definition (DTD). DTD is intended to be a way to define the legal building blocks of an XML document. This is done by defining elements and entities. Entities are commonly used to define constant values that can be referenced within the XML. DTD can be defined locally or by importing a .dtd file from a SYSTEM (local) or PUBLIC (remote) source.
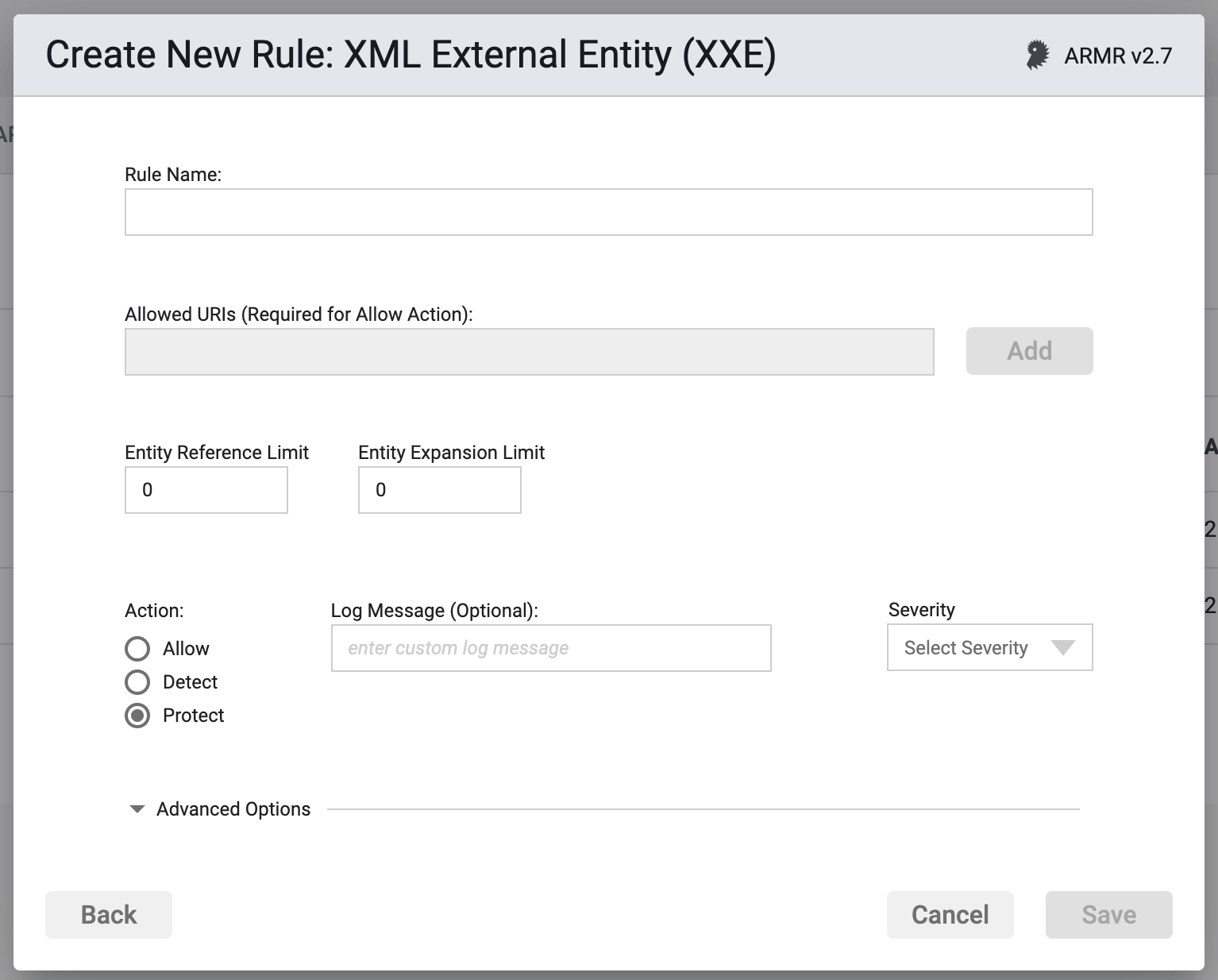
Rule Options
Allowed URIs
A rule configured with the Allow Action gives application owners the ability to permit certain URIs defined in the XML to be accessed. URIs can only be defined when the rule's Action is set to Allow URIs. The entries can be system or public URIs/URLs, declared within the DTD that would otherwise be considered as an attack. When any defined URI within this rule is identified in runtime, the application will continue as normal and a log message will be generated with details of the event.
The Allow Action is used in conjunction with a second XXE rule configured with a Protect Action. Changing the XXE rule configured with an action of Protect to Detect will help identify any URIs that may need to be allowed. Once identified, the URI parameter can be configured to allow only those specific URIs. Attempts to access URIs outside of the list will be blocked.
Entity Limits
The entity limits are two user-defined thresholds that individually trigger an ARMR security response when exceeded. The Entity Reference Limit and Entity Expansion Limit can only be defined when the rule's Action is set to Protect. When both limits are defined as 0 then no limits are applied.
When a system reads XML files with a number of general entity references, the Entity Reference Limit sets the threshold number allowed before the ARMR rule triggers. Similarly, when an expanded string is used, the Entity Expansion Limit sets the threshold for the max expanded string length allowed before the rule is actioned. In both cases, the default value is 0.
Action
- Detect - The Agent will Detect an attack, log the event to the event database and the event will be viewable on the Security Events pages in the Portal, but the Agent will take no further action
- Protect - In addition to the Detect actions, the Waratek Agent will also actively prevent the attack from succeeding.
- Allow - The Agent will Allow access to user defined URIs and log the event to the event database noting that the URI that has been allowed.
Log Messaging
The logs provide a message field, which can be customized. Text entered here is the message that will be seen on the log files when the rule has been triggered, regardless of the Action. If the field is left blank, then the default logging message will be displayed in the message portion of the event log.
Severity
The log files allow you to select a custom severity level for the event: Low, Medium, High or Critical. A severity is required, and there is no default selection.
Advanced Options
Disable Logging - By checking this option, no logging will be performed when a rule is triggered. Subsequently the Portal will not see these events, and they will not appear anywhere in the Portal, nor will they be searchable in Event Storage.
This option will be greyed out if the rule action is set to Detect.
Enable Stack Trace - By checking this option, when a rule is triggered, the stack trace will be included in the event log, and will be available for viewing in the Portal UI for each triggering security event.